Windows 7 was End-of-Life’d on January 14, 2020, and Microsoft’s Extended Security Update (ESU) plan, available to select customers, ended on January 10, 2023. Without ongoing support, cybersecurity attacks on this older operating system are rising. Most modern enterprises have migrated at least to Windows 10 to comply with security regulations and concerns. Yet, there is a huge number of PCs that have yet to upgrade. Why is that, what vulnerabilities are these exposed to, and what are the mitigations employed by more current operating systems?
Long before Windows 7 went End-of-Life (EOL), my company, ASSET InterTech, upgraded all systems, enterprise-wide, to Windows 10. Being a responsible member of the supply chain, and needing to protect our own assets as well as those of our customers and suppliers, made this a logical choice. As well, to ensure that we are in compliance with the most advanced quality management practices, we’ve been certified to ISO 9001:2015; and we are on a journey to Level 2.0 certification of the Cybersecurity Security Maturity Model (CMMC), as my colleague Keith Stephenson wrote about here: Our Cybersecurity Maturity Model Certification (CMMC) Compliance Initiative. In Keith’s words,
“CMMC is based off of the NIST 800-171 (NIST – National Institute of Standards and Technology). This is the standard to protect CUI ( Controlled Unclassified Information) data in nonfederal systems and organizations. These controls are not just protecting the CUI data a nonfederal entity has access to, but also the environment around this data. ASSET InterTech is focused on providing the most secure environment to protect our Defense Suppliers’ information with protected controls of the data, as well as protective controls of our work environment, by securing end user endpoints, network, virtual machines, etc. NIST 800-171 has 110 Controls that are tracked by the CMMC assessors and are the foundation of securing CUI data.”
This requires rigorous implementations of information access control, encryption, firewalls, intrusion detection/prevention systems, penetration testing, cybersecurity training, and many other details. It’s hard work, but it’s worth it.
As a technologist with a keen interest in cybersecurity, I’m very aware of how complex and multi-layered a subject like this is. In 2019, I received the Walter E. Peterson Best Technical Paper Award for my Mitigating JTAG as an Attack Surface at the AUTOTESTCON conference, a premier event for the military/aerospace automated test industry. This paper explored the ways that JTAG, a technology that is inherent in almost all semiconductors, could be attacked and defended. And more recently, I presented an overview article on The Windows 7 Attack Surface, as a way to raise awareness of how vulnerable Windows 7 actually is. I’m going to recap some of the highlights of that presentation here.
Agenda
In this presentation, I’ll cover the main topics associated with what makes Windows 7 so vulnerable, what the attack vectors are, and what makes Windows 10 much more secure.
The topics we’ll cover in the slides are:
- Why is the Windows 7 attack surface important?
- The lifecycle of Windows 7/10/11
- The advancing thread landscape
- Rootkits: Windows 7 vulnerabilities
- Mitigating threats with Windows 10
- Bootkits: UEFI vulnerabilities
- “Chipkits”: Silicon vulnerabilities
Why is the Windows 7 attack surface important?
Windows 7 End-of-Life occurred going on four years ago. And although some select customers paid for the Extended Security Update (ESU) plan, that itself ended at the beginning of 2023.
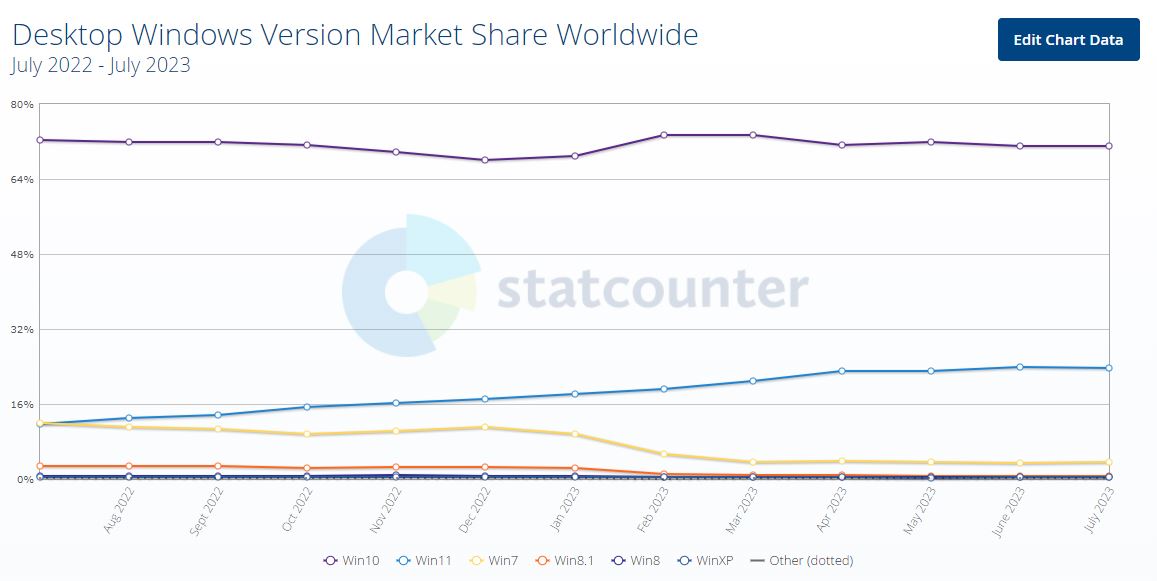
According to GlobalStats, the market share of Windows 7 (as a percentage of roughly 1.4 billion Windows PCs worldwide) hovered around 11% through 2022. When the ESU ended, its penetration started to plummet, going down to roughly 3.7% as of July 2023. This is reassuring, of course, to some extent; but as you can see from the graph below, the Windows 7 penetration has flattened out since the spring. And 3.7% of 1.4 billion PCs still leaves about 52 million of these vulnerable machines in use:
Many Windows 7 PC users consider their machines to be secure because they are not connected to the Internet. This does indeed make it more difficult for attackers to deliver a payload to a target machine. But consideration should be given to other attack vectors whereby a PC can be infected: bluetooth, through a rogue USB stick insertion, latent bootkits and rootkits (to be discussed later), and other mechanisms. Certainly, if a bad actor has physical access to a Windows 7 machine, it’s game over – it becomes a very simple matter to “own” the machine. And zero-day vulnerabilities, that have been in Windows 7 since its early days and are still being discovered, make a ripe pathway for a malfeasant to exploit vulnerabilities.
For defense and aerospace systems within the USA, it is quite common to require an Authority to Operate (ATO) prior to operating a known vulnerable system. An ATO is a formal declaration by a Designated Approving Authority (DAA) that authorizes operation of a Business Product and explicitly accepts the risk to agency operations. In other words, the benefits of continuing to operate the system outweigh its security risk.
Windows 7/10/11 Lifecycle
The key dates associated with Windows 7, 10 and 11 releases are as follows:
Windows 7
- Initial release: October 22, 2009
- End-of-Life: January 14, 2020
- End of Extended Service Updates (ESU): January 10, 2023
Windows 10
- Initial release: July 29, 2015
- End-of-Life: October 14, 2025
- Forecasted end of ESU: ~ 2030
Windows 11
- Initial release: October 5, 2021
- Builds on Windows 10, with updated UI and better WSL 2 support
- Modern CPU + TPM requirement
Although Microsoft does intend to EOL Windows 10 in a couple of years, we might expect the ESU to extend perhaps through the end of this decade.
Windows 11 is, of course, the most secure and modern operating system for general desktop use. However, it presented a disruption in the context of having a set of minimum system requirements, especially in the context of needing a more modern CPU, and the PC having a Trusted Platform Module (TPM). These more stringent hardware requirements make it a more expensive upgrade than simply going from Windows 7 to Windows 10.
The Advancing Threat Landscape
Escalating layers of security within platform software and firmware are defined as “Rings”, with Ring 3, User Mode, being the least privileged, and Ring -3, System Management Mode or SMM, being the most privileged. Many thanks to Pavel Yosifovich, software developer, trainer, and co-author of “Windows Internals” 7th edition (2017), “Windows Kernel Programming” (2019), “Windows 10 System Programming Part 1” (2020) and Part 2 (2021), as well as “WPF 4.5 Cookbook” (2012); for the use of the images from his Windows Internals course.
Rootkits are defined as attacks that use Windows internals, such as those that corrupt the kernel and hypervisor. Bootkits inject themselves into platform firmware such as the UEFI (also known as BIOS) or SMM. I was introduced to these concepts by reading the book Rootkits and Bootkits by Alex Matrosov, Eugene Rodionov, and Sergey Bratus. The cover art is worth the price of the book:
Alex has gone on to found the company Binarly, a company that delivers an advanced automated firmware supply chain security platform. Using cutting-edge machine-learning techniques, Binarly’s solution identifies vulnerabilities, misconfigurations, and malicious code in firmware and hardware components. And the lower in the ring hierarchy the protection is, the more protection is provided.
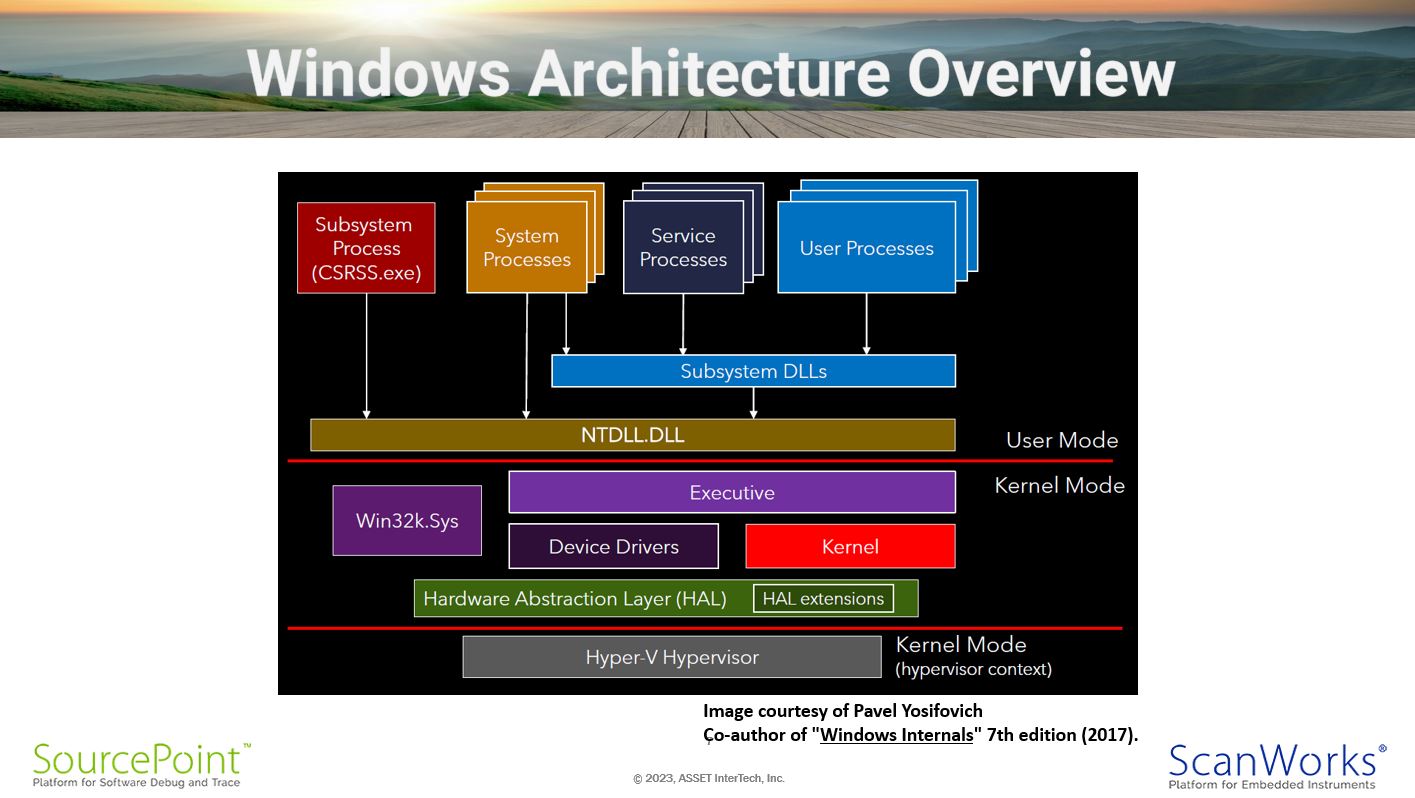
Windows Architecture Overview
It’s helpful to see the overall Windows architecture, in terms of understand where the attack surfaces may be. Early intrusions were done up in User Mode. These tended to not be persistent, and were easily defended against. Over time, attackers became more sophisticated, and moved their attention to the Windows kernel. Malware, antivirus, and other defensive software in turn adapted to detect and mitigate against these; a thriving industry of Endpoint Detection and Response (EDR) software companies grew out of this, with players such as CrowdStrike, Norton, Symantec, Rapid7, and many other selling directly to enterprises. It may forever be a “cat-and-mouse” game between new creative attacks and the software and firmware that protects us against them.
Kernel Mode Components
This slide provides more detail on some of the individual kernel components:
- Hardware Abstraction Layer (HAL)
- Isolates the kernel and device drivers from platform specific aspects
- Kernel
- Thread scheduling, interrupt and exception dispatching, multiprocessor support, synchronization primitives
- Device Drivers
- Loadable kernel modules, classically handle I/O requests for hardware devices and buses
- Executive
- Memory manager, object manager, security, plug & play manager, power manager, configuration manager, etc.
- sys
- The Windows subsystem kernel-mode component
- Handles user interface and graphics
Although the information is dated, in 2018 Microsoft published the sizes of some of the kernel mode components. I’d guess that there’s been significant growth since then:
| Kernel subsystems | Lines of code |
| Memory Manager | 501, 000 |
| Registry | 211,000 |
| Power | 238,000 |
| Executive | 157,000 |
| Security | 135,000 |
| Kernel | 339,000 |
| Process sub-system | 116,000 |
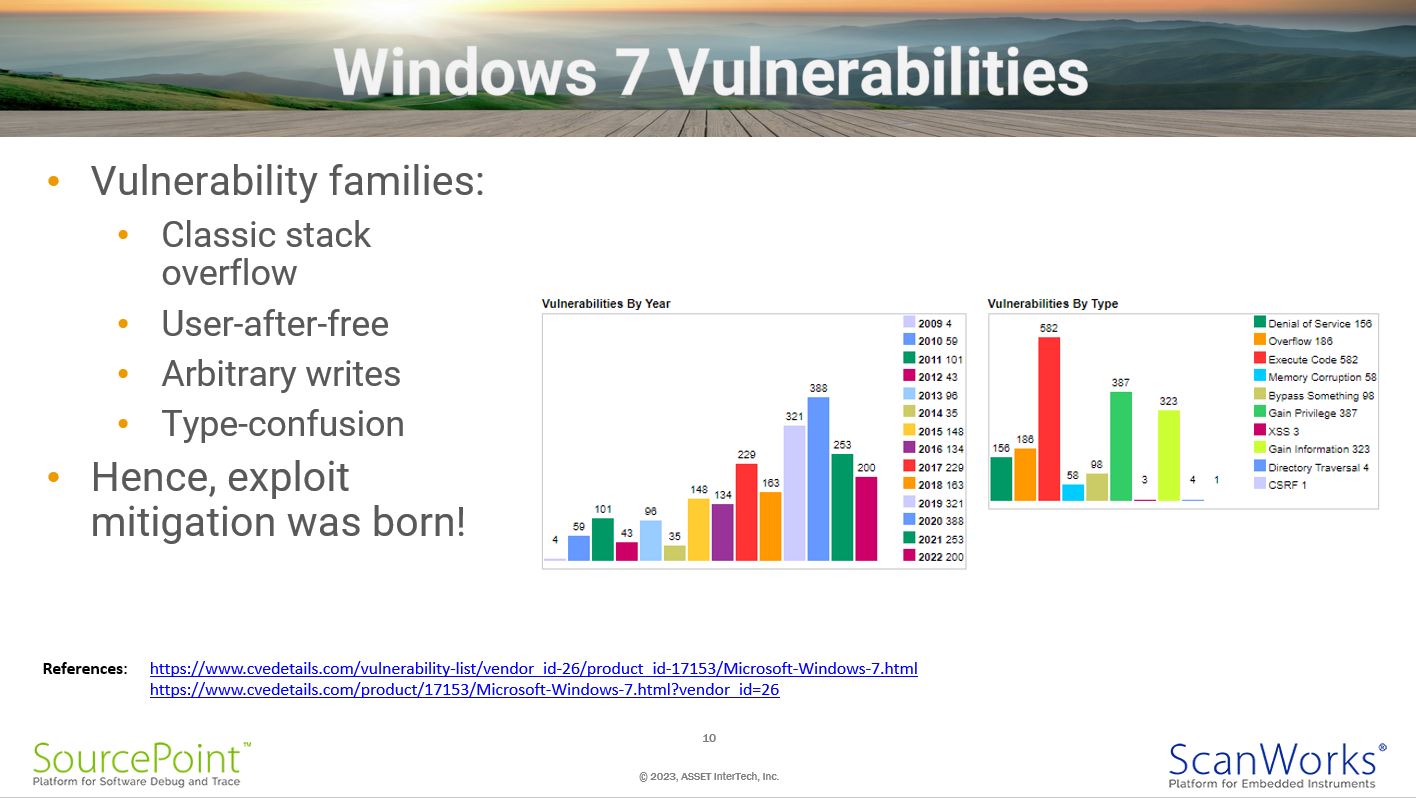
Windows 7 Vulnerabilities
A comprehensive list of known Windows 7 vulnerabilities is available here: https://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-17153/Microsoft-Windows-7.html.
And a summary of Vulnerability Statistics is here: https://www.cvedetails.com/product/17153/Microsoft-Windows-7.html?vendor_id=26.
Vulnerabilities such as the classic stack overflow, user-after-free, and type-confusion can be used to execute arbitrary code that corrupts the Windows 7 kernel.
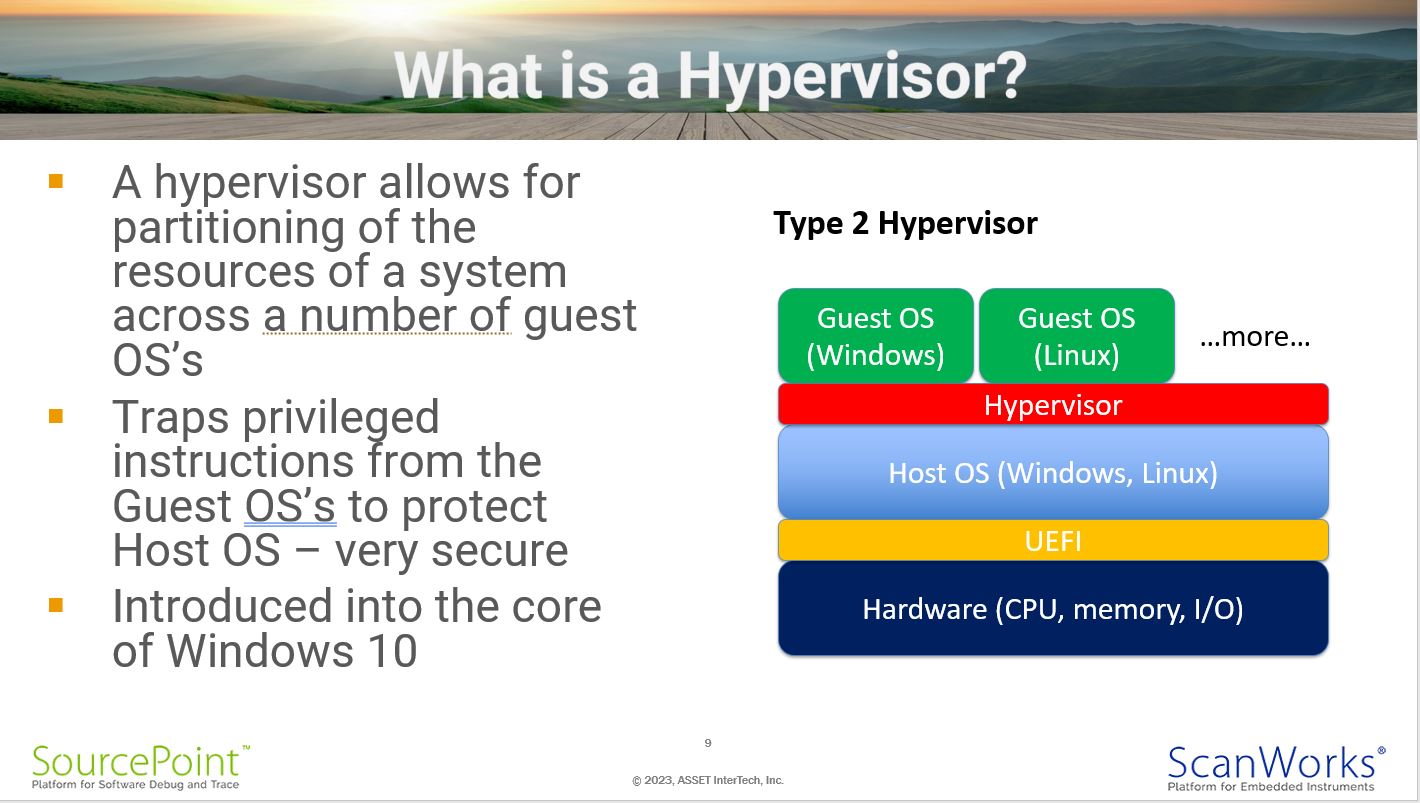
What is a Hypervisor?
From the previous slides, you can see a hypervisor at the foundation of Windows. This was introduced initially with Windows 10. Hypervisors were created firstly to provide support for virtual machines – this was a game-changer in the server industry, wherein a single physical server can now host multiple guest operating systems with their associated applications, with much more efficient use of hardware resources. It became clear to Microsoft that this technology could also be used to trap privileged instructions executing on a single host – preventing unauthorized attacks on the kernel and creating a much more secure framework – so they integrated it into the foundation of Windows 10.
Windows 10 Mitigations
As such, a bunch of new mitigations were incorporated into Windows 10, among them:
- Protected Process Light (PPL)
- Address Space Layout Randomization (ASLR)
- Virtualization-based Security (VBS)
- Credential Guard
- Control Flow Guard (CFG)
- HyperGuard
- PatchGuard
- KMCS
- HVCI
- Data Execution Prevention (DEP)
- Page Table Randomization
- Arbitrary Code Guard (ACG)
- Control Enforcement Technology (CET)
I’ll touch on just a couple of these for background.
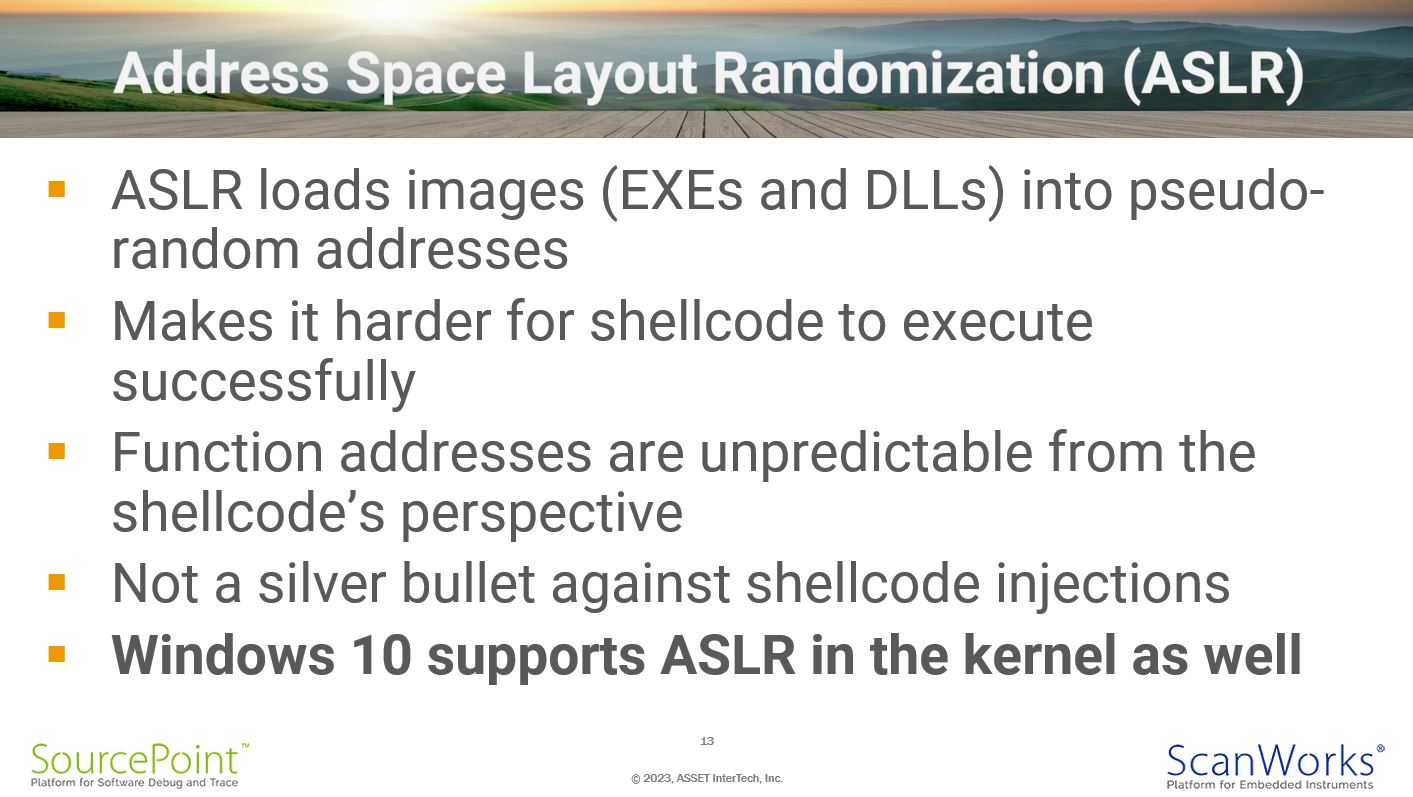
Address Space Layout Randomization (ASLR)
Address Space Layout Randomization is a mechanism that has been used for quite some time, that randomizes user space base, libraries, heap, and stack at random positions in a process’s address space. This makes it difficult for malicious code to predict the memory address of the next instruction. Starting with Windows 10, this protective mechanism was built into the kernel.
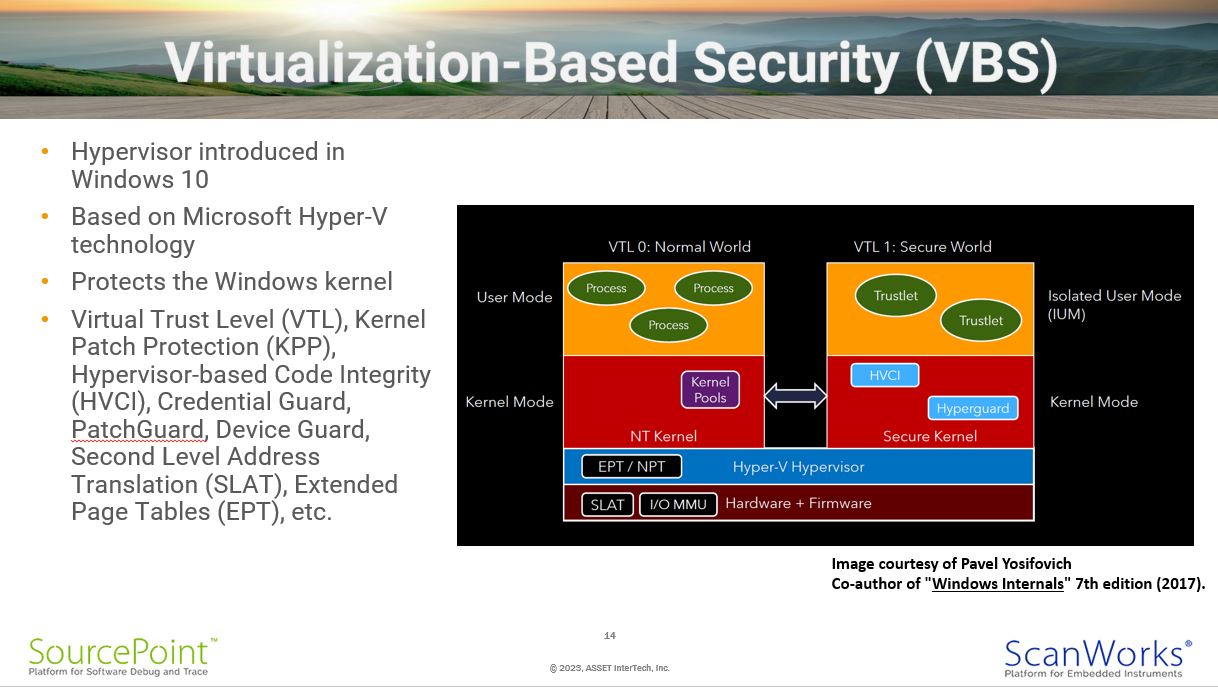
Virtualization-Based Security (VBS)
Virtualization-Based Security (VBS) uses hypervisor technology, built into the Windows core as of Windows 10, that Microsoft developed as part of its Hyper-V virtualization machine monitor. The separation of Windows into User Mode and Kernel Mode has long protected the kernel from issues originating within user mode code. However, if an unwanted kernel modification were made, either through an existing vulnerability or when a user installed a malicious kernel driver, the whole system is compromised. Remember, in Windows 7, kernel mode code has access to the entire system. With Windows 10, an additional level of privilege separation is introduced through Virtual Trust Levels (VTLs), labeled VTL 0 and VTL 1. VTL 1 provides an additional layer of trust by running its own secure kernel within Ring 0.
VBS introduces a slew of supported technologies such as Kernel Patch Protection (KPP), Hypervisor-Based Code Integrity (HGCI), Credential Guard, and so on. All available only on Windows 10 and above.
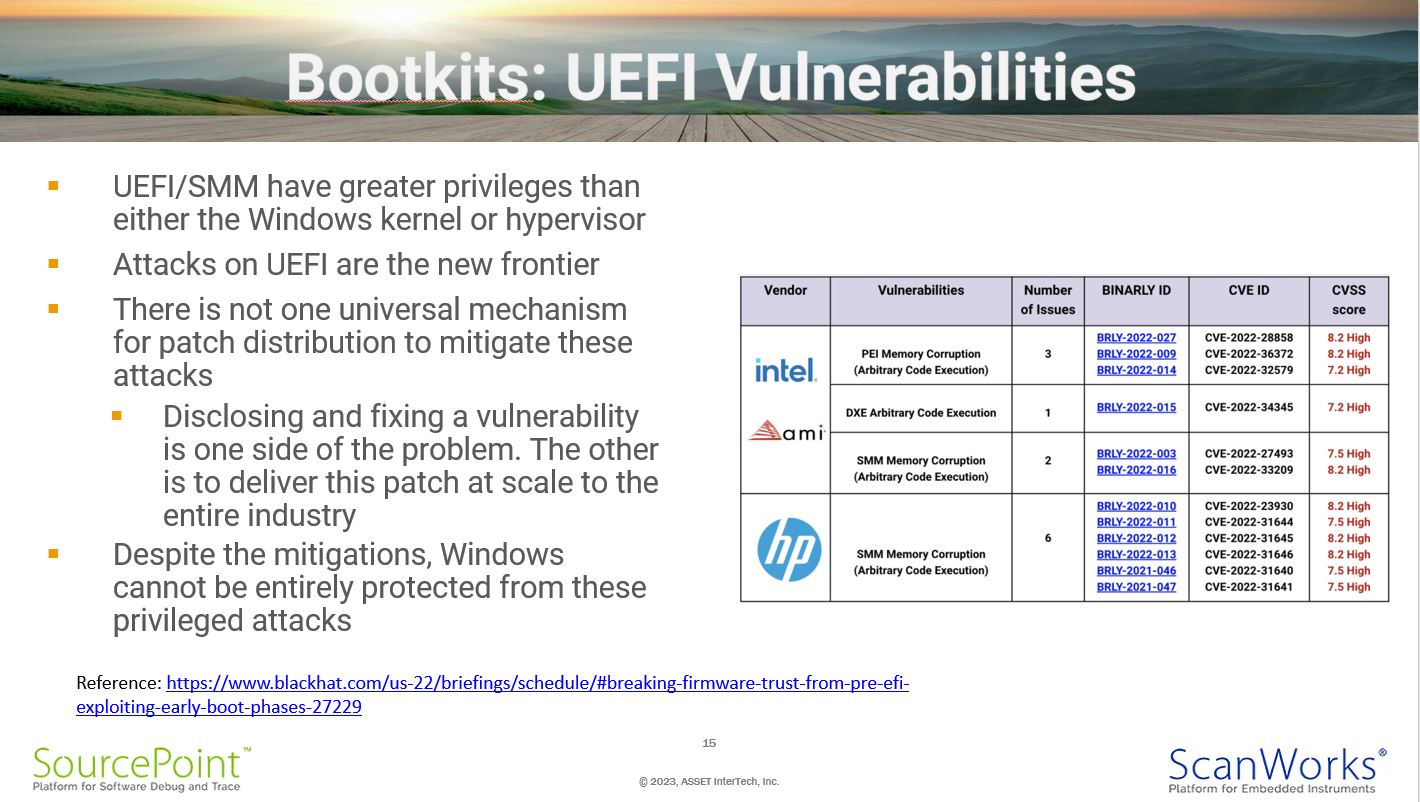
Bootkits: UEFI Vulnerabilities
I’ve spoke about Bootkits at length above. These originate below Windows, and if flashed onto a PC motherboard, are entirely persistent. By design, much of the UEFI code is not reused once Windows boots. But, if the infection mechanism of malicious code within the UEFI image is used to corrupt the Windows kernel, or if the errant code is part of UEFI runtime services, these will persist and lay dormant until activated. With Windows 7 being so much more vulnerable to kernel corruptions, such intrusions can go unnoticed and undetected.
“Chipkits”: Silicon Vulnerabilities
Although a little orthogonal to a discussion on Windows 7 vulnerabilities, it is worthwhile noting the research into trojans within the chips themselves is very active. For those interested in further reading, I’d suggest Tunable Replica Circuit for Fault Injection Detection, a presentation by Intel at Black Hat USA 2022; and my blog Using JTAG for Silicon Trojan Detection and Mitigation.
Wrap-Up
This slide really speaks for itself. Having been EOL’ed for over three years now, and protection via the Extended Security Update having ended earlier this year, Windows 7 machines are now more vulnerable than ever before. In my humble opinion, it’s only a matter of time before major cyberincidents happen to fleets of Windows 7 machines.